 Dastardly, from Burp Suite
Free, lightweight web application security scanning for CI/CD.
View all product editions
Dastardly, from Burp Suite
Free, lightweight web application security scanning for CI/CD.
View all product editions
 Dastardly, from Burp Suite
Free, lightweight web application security scanning for CI/CD.
View all product editions
Dastardly, from Burp Suite
Free, lightweight web application security scanning for CI/CD.
View all product editions
How many times have you seen this?
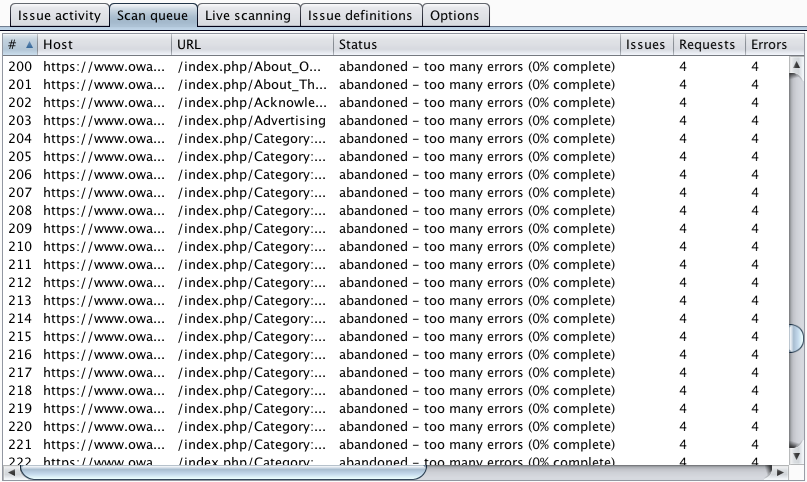
As we have already described, Burp's current Scanner processes each item in the scan queue in isolation. If it runs into connection errors and transmission timeouts, then it eventually abandons the item and moves on to the next. There are two quite annoying limitations in this approach:
Burp's new Scanner addresses these issues with a robust approach to handling application errors. This comprises the following key elements:
There are separate options to configure how Burp handles application errors during the crawl and audit phases of a scan:
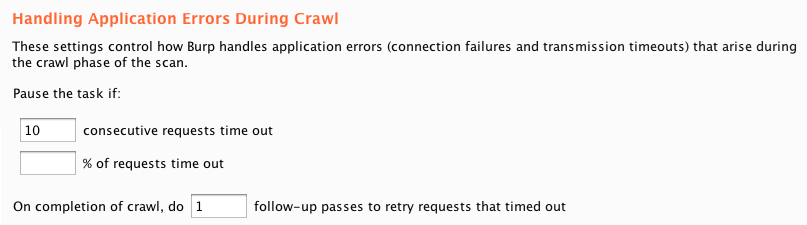
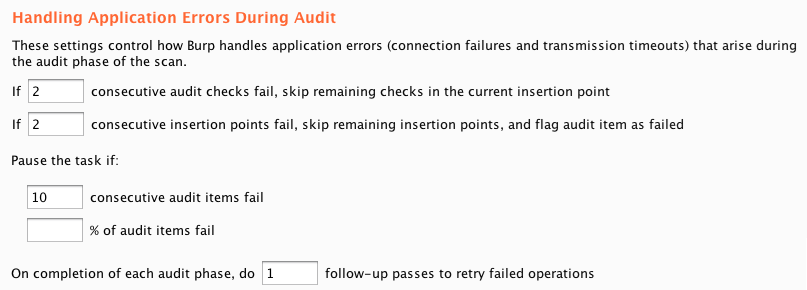
The ability to track errors at a granular level and bubble up when repeated errors occur is particularly useful during the audit phase of a scan. Burp tracks errors first at the level of individual audit checks, then individual insertion points, then the request that is being audited, and ultimately the entire scan. This nicely deals with web application firewalls that might selectively drop connections based on specific payloads that are used in some audit checks, and also cases where they drop connections that make any modifications to a specific parameter.